 A evolução das redes WAN e da segurança de rede tem sido rápida nos últimos 20 anos.
A evolução das redes WAN e da segurança de rede tem sido rápida nos últimos 20 anos.
Antes de 2000, as redes WAN eram relativamente simples, com redes privadas (como MPLS e linhas alugadas) combinadas com firewalls centralizados colocados nas sedes e nos data centers.
Naquela época, a maioria dos funcionários trabalhava no escritório e estava presa a um cabo; não havia nuvem para falar.
Os funcionários remotos eram conectados a um concentrador de VPN central.
Embora as redes privadas proporcionassem uma experiência controlada de alto desempenho, elas eram caras.
No entanto, com o número limitado de funcionários remotos, uma experiência abaixo da média não era considerada um problema significativo.
Quase não havia firewalls nas filiais, e um firewall localizado centralmente protegia as conexões com a Internet.
As equipes de rede e segurança eram organizadas em silos separados e só ocasionalmente colaboravam umas com as outras.
Nos últimos 25 anos, uma série de novas tecnologias interrompeu a ordem estabelecida, incluindo Wi-Fi em 1997, Internet de banda larga em 2000, otimização de WAN em 2002, serviços em nuvem em 2006, segurança em nuvem em 2008, SD-WAN em 2012 e SASE (Secure Access Service Edge) em 2019.
Como resultado, as organizações de TI e segurança têm se debatido com três questões fundamentais: Primeira pergunta: onde colocar o ponto de acesso à Internet? Antes de o Wi-Fi se tornar onipresente, era prática comum rotear todo o tráfego da Internet pela WAN privada para um local central onde um conjunto de firewalls protegeria o perímetro da empresa.
No entanto, à medida que a adoção do Wi-Fi e da nuvem se tornou mais difundida, o encaminhamento de grandes quantidades de tráfego da Internet por links privados caros começou a comprometer o desempenho dos aplicativos.
Consequentemente, houve uma tendência crescente de colocar o breakout da Internet nas filiais e implantar firewalls nesses locais, apesar do custo adicional e do maior risco de segurança.
A segurança na nuvem veio em socorro em 2008, fornecendo uma solução ideal para escritórios menores e trabalhadores remotos, permitindo que eles mantivessem os firewalls longe do local e eliminassem o hair-pinning para os usuários remotos.
Para grandes sites e data centers, o NextGen Firewall no local permaneceu em vigor, criando o desafio de que as políticas de segurança agora estavam divididas entre a segurança na nuvem e no local. Segunda pergunta: Como a Internet mais barata pode ser usada para reduzir os custos de WAN das empresas? A maioria das empresas se absteve de conectar os escritórios diretamente à Internet por motivos de simplicidade e segurança.
No entanto, à medida que a adoção do Wi-Fi e da nuvem forçou as mãos dos gerentes de TI e a Internet foi introduzida em todos os escritórios, a conectividade com a Internet passou a ser vista cada vez mais como uma oportunidade de reduzir as despesas com a WAN.
Isso impulsionou a adoção da SD-WAN, que usava recursos de direção e otimização de caminhos para fornecer o desempenho necessário dos aplicativos usando o caminho ideal (Internet ou MPLS) quando necessário.
O maior benefício da SD-WAN foi a redução de custos, diminuindo ao máximo a necessidade de MPLS caro (e inflexível) ao direcionar o tráfego da WAN pelos circuitos da Internet.
Hoje, muitas empresas até eliminaram totalmente o MPLS e o substituíram por links (duplos) de Internet.
No entanto, a Internet é uma tecnologia de melhor esforço com latências inconsistentes e sem garantias de largura de banda.
Isso criou a necessidade emergente de uma Internet aprimorada com garantia de tempo de atividade e latências mais previsíveis.
Além disso, com a explosão de aplicativos na WAN, os gerentes de rede querem eliminar qualquer causa de desempenho inferior dos aplicativos.
Além disso, com o aumento do trabalho em qualquer lugar, ficou evidente que os funcionários remotos precisariam desfrutar da mesma experiência que os funcionários do escritório.
As soluções SD-WAN tradicionais se concentravam principalmente na conectividade do escritório, o que geralmente resultava em maior complexidade da rede e maior sobrecarga de gerenciamento. Terceira pergunta: Qual arquitetura de nuvem em rampa se adapta melhor às necessidades de nuvem em constante mudança? Com a adoção generalizada de serviços em nuvem, as empresas agora estão lidando com o desafio de gerenciar conexões entre sua WAN e os provedores de nuvem.
Isso exige onramps de nuvem específicos que agregam conexões de vários escritórios e usuários remotos em um único link para o local de IaaS de um provedor de nuvem específico.
Os onramps de nuvem são caros, pois cada on-ramp requer pontos de agregação específicos em um local específico.
Além disso, esses on-ramps de nuvem devem se encaixar na estrutura geral de segurança da empresa, que geralmente envolve uma combinação de firewalls locais e segurança de nuvem que abrange tanto o caso de uso de breakout da Internet quanto as conexões site a site. O resultado final: As organizações de TI estão presas a redes Frankenstein”. As organizações de TI têm se esforçado para encontrar respostas simples para as três perguntas mencionadas acima e agora estão enfrentando uma situação complexa e desafiadora.
Elas ficam com uma colcha de retalhos de implementações separadas de SDWAN para conectar filiais, nuvem-onramps e implementações de segurança para nuvem e segurança no local.
Essas diferentes implementações geralmente vêm de vários fornecedores e com ferramentas de gerenciamento separadas, levando a uma solução complexa e incômoda de gerenciar e manter.
Essa “rede Frankenstein” é complexa e resulta em desempenho abaixo da média, políticas de segurança inconsistentes e falta de visibilidade e controle, o que dificulta a resolução de problemas de forma rápida e eficiente. 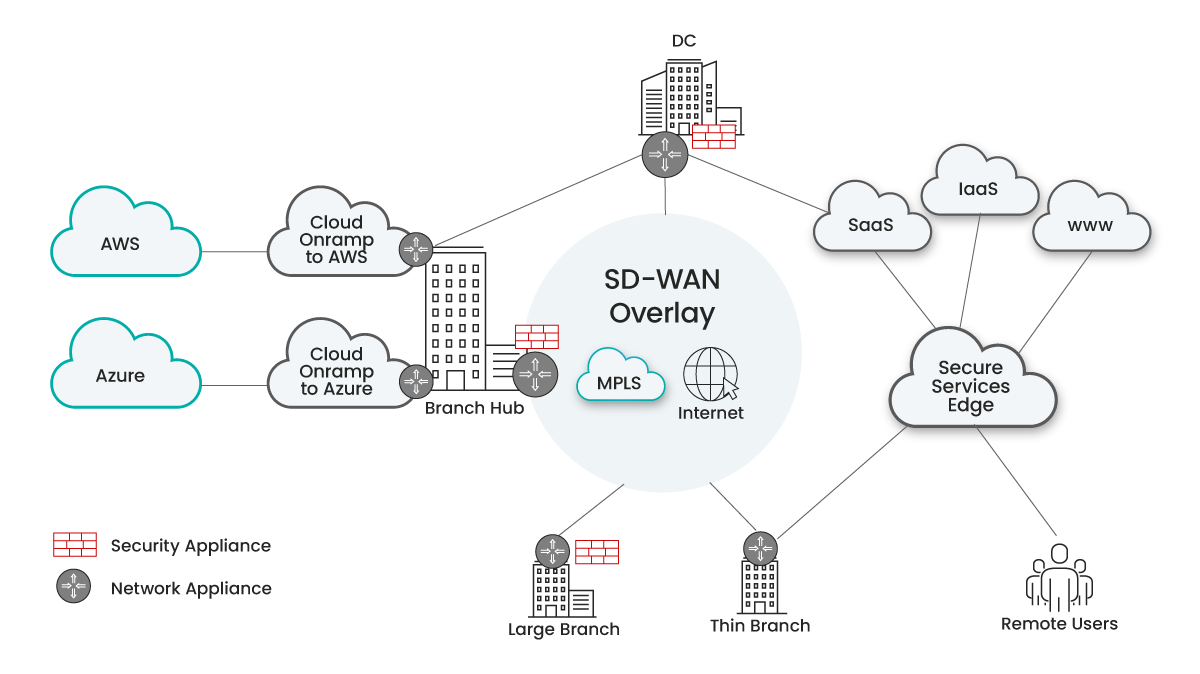
As redes Frankenstein típicas de hoje
“Solução SASE da Aryaka: O fim das redes Frankenstein”
O surgimento das redes Frankenstein deixou as organizações de TI em busca de uma solução, e a SASE surgiu como a resposta.
A abordagem da Aryaka para a SASE começa com uma base de rede de alto desempenho, permitindo conexões seguras entre usuários e aplicativos, independentemente do local, tudo sob um conjunto de políticas totalmente unificadas para rede e segurança.
Ao aplicar políticas de segurança o mais próximo possível dos usuários e aplicativos, seja na nuvem ou no local, os gargalos de desempenho são eliminados em conformidade com os princípios de confiança zero.
A base da rede deve eliminar o patchwork inflexível de redes separadas que conectam filiais, usuários, data centers e a nuvem e ser fornecida como um serviço de nuvem consumível, incluindo a funcionalidade no local.
Além disso, uma infraestrutura de rede flexível deve oferecer três níveis de serviço para otimizar as despesas da WAN: internet de melhor esforço, melhor que a internet e melhor que o MPLS, eliminando completamente o MPLS legado.
Muitas vezes, vale a pena observar que as implementações atuais de SASE de um único fornecedor parecem ser soluções SASE no nível superficial, mas, por baixo do capô, elas ainda podem ser redes Frankenstein que não limparam a arquitetura subjacente. 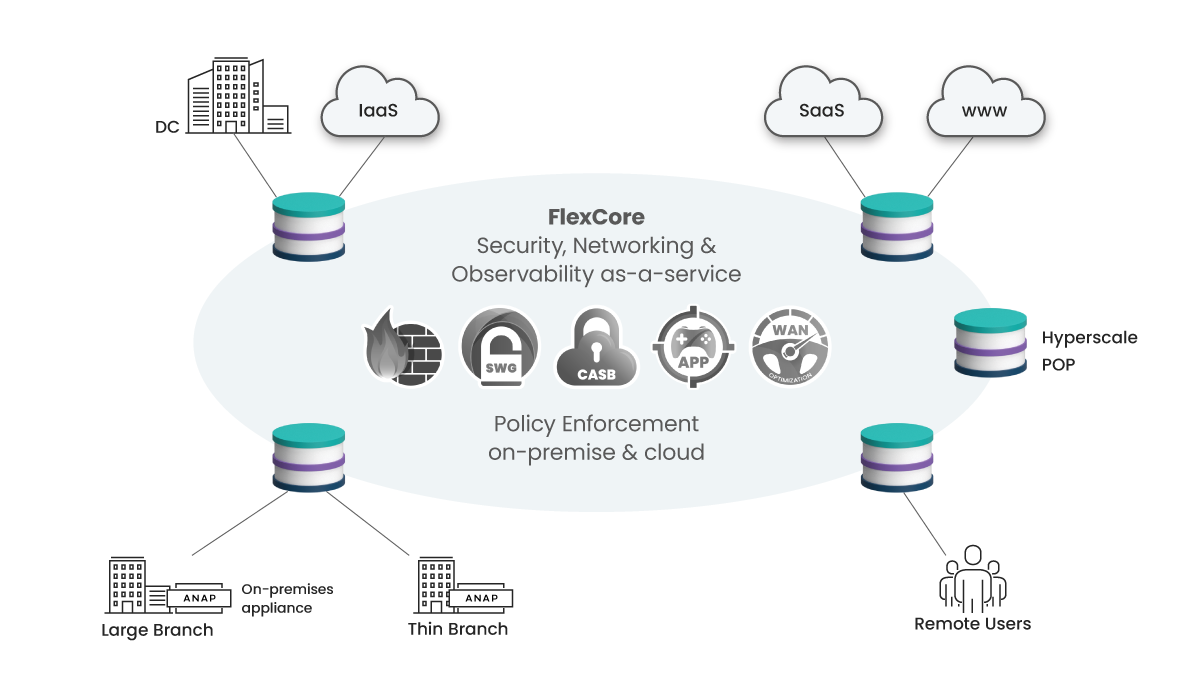
SASE unificado da Aryaka no FlexCore Foundation
Os resultados da abordagem da Aryaka fornecem uma solução SASE fácil de consumir que beneficia os clientes ao oferecer uma experiência altamente segura e de alto desempenho para todos os usuários, aplicativos e cargas de trabalho.
Esse consumo fácil é estabelecido por uma infraestrutura nativa da nuvem que consiste no controle determinístico da subcamada da rede, combinado com uma arquitetura de caminho único de funções de rede, otimização e segurança com fluxos de trabalho de serviço integrados.
Agilidade e flexibilidade são as principais vantagens para os clientes, pois agora eles podem evoluir sua infraestrutura de rede e segurança no ritmo da transformação digital sem fim.
Além disso, com essa abordagem, os usuários podem se mudar rapidamente e as filiais podem ser realocadas sem a necessidade de substituir constantemente as tecnologias e os fornecedores a cada poucos anos, à medida que surgem novos desafios.
Além disso, as onipresentes nuvens caras podem ser eliminadas sem a necessidade de atualizações dispendiosas na infraestrutura de rede.
Os SLAs (Service Level Agreements, acordos de nível de serviço) de rede, que vão desde o melhor esforço até o desempenho garantido dos aplicativos, podem ser alterados instantaneamente com base nas necessidades dos usuários e na natureza dos aplicativos.
A solução SASE da Aryaka, com seu consumo fácil, agilidade, flexibilidade e serviços gerenciados, oferece aos clientes uma ferramenta poderosa para eliminar as redes Frankenstein e assumir o controle de sua infraestrutura de rede e segurança.